In This Article
Scam Messaging and Impersonation
Scams can come in email, text, phone calls or messaging apps.
Be aware of any communications that attempt to manipulate you into giving up information about yourself, others or the university or ask you to take any action with data or money (gift cards are a common request). Often these types of messages attempt to impersonate people you know or people in a leadership position. Always verify through another source if you are being asked to make any purchase or provide information.
Here is a quick video with some pointers. (login required)

Here are a few recent examples of scam messages to avoid.
Phishing Awareness
Email phishing is the favorite tool of criminals. The bad guys are using phishing attacks for nearly every cybercrime on their list. Identity theft, ransomware, extortion, financial fraud and nearly all major breaches in the news start with a phishing email. The COVID-19 pandemic in particular saw a massive surge in phishing that attempted to exploit people's views or fears of the virus.
Olivet has partnered with the company KnowBe4 to provide resources for training on how to identify and avoid Phishing emails.

Below is a video provided by KnowBe4 called "The Art of Phishing" (login required) that talks about the key elements that scammers want to include in their messages and how they try to trick you.

Phish-Fridays
Olivet has partnered with KnowBe4 to implement Phish-Fridays.
Every Friday, a rotating portion of ONU mailboxes will receive simulated phishing emails that are based on real-world phishing attacks. If you click on the link in the email, you be directed to a dynamic KnowBe4 page with advice on how to spot Phishing emails and some red flags in the simulation you received (example below).

What Is In the KnowBe4 Training?
KnowBe4 offers a whole suite of cybersecurity training that includes topics beyond phishing, so there could be many other resources that are available to you. However, phishing awareness will be available to everyone within the KnowBe4 portal.
Dashboard
The dashboard shows a snapshot of your activity related to phishing simulations, an overview of your assigned modules and your ONU account's risk exposure based on your actions and position in the university.

Training
The training tab shows you the modules that are assigned to you. These could be videos, interactive training modules, security assessments or other content. From this page you can start or resume any of the content that is available to you.

Library
This section shows content that is not assigned to you, but is available to everyone to complete at any time. By default, everyone should have access to a few interactive games that are fun ways to learn about some security concepts.

How Do I Report Phishing Messages?
Use the Phish Alert button.
The Phish Alert button will report offending messages to our security team and the KnowBe4 system.
Where is the Phish Alert Button?
The Phish Alert button is in different places depending on how you are reading your email. In general, you need to be using one of Microsoft's products: Outlook for Windows, iOS or Android or through email.olivet.edu. Below are a few pointers on where to find the Phish Alert button.
|
Outlook for Windows:
|

|
|
Outlook Web Access
or

|

If you do not see this icon, you will need to add it. See this video.
|
|
Outlook app on iOS
|

|
|
Outlook app on Android
|

|
Know More About Phishing.
Phishing is the process of attempting to acquire sensitive information such as usernames, passwords and credit card details by masquerading as a trustworthy entity using bulk email which tries to evade spam filters.
Emails claiming to be from popular social web sites, banks, auction sites, or IT administrators are commonly used to lure the unsuspecting public. It’s a form of criminally fraudulent social engineering.
Techniques
There are a number of different techniques used to obtain personal information from users. As technology becomes more advanced, the cybercriminals' techniques being used are also more advanced. To prevent Internet phishing, users should have knowledge of how the bad guys do this and they should also be aware of anti-phishing techniques to protect themselves from becoming victims.
-
Spear Phishing
Think of spear phishing as professional phishing. Classic phishing campaigns send mass emails to as many people as possible, but spear phishing is much more targeted. The hacker has either a certain individual(s) or organization they want to compromise and are after more valuable info than credit card data. They do research on the target in order to make the attack more personalized and increase their chances of success.
-
Session Hijacking
In session hijacking, the phisher exploits the web session control mechanism to steal information from the user. In a simple session hacking procedure known as session sniffing, the phisher can use a sniffer to intercept relevant information so that he or she can access the Web server illegally.
-
Email/Spam
Using the most common phishing technique, the same email is sent to millions of users with a request to fill in personal details. These details will be used by the phishers for their illegal activities. Most of the messages have an urgent note which requires the user to enter credentials to update account information, change details, or verify accounts. Sometimes, they may be asked to fill out a form to access a new service through a link which is provided in the email.
-
Content Injection
Content injection is the technique where the phisher changes a part of the content on the page of a reliable website. This is done to mislead the user to go to a page outside the legitimate website where the user is then asked to enter personal information.
-
Web Based Delivery
Web based delivery is one of the most sophisticated phishing techniques. Also known as “man-in-the-middle,” the hacker is located in between the original website and the phishing system. The phisher traces details during a transaction between the legitimate website and the user. As the user continues to pass information, it is gathered by the phishers, without the user knowing about it.
-
Phishing through Search Engines
Some phishing scams involve search engines where the user is directed to product sites which may offer low cost products or services. When the user tries to buy the product by entering the credit card details, it’s collected by the phishing site. There are many fake bank websites offering credit cards or loans to users at a low rate but they are actually phishing sites.
-
Link Manipulation
Link manipulation is the technique in which the phisher sends a link to a fake website. When the user clicks on the deceptive link, it opens up the phisher’s website instead of the website mentioned in the link. Hovering the mouse over the link to view the actual address stops users from falling for link manipulation.
-
Vishing (Voice Phishing)
In phone phishing, the phisher makes phone calls to the user and asks the user to dial a number. The purpose is to get personal information of the bank account through the phone. Phone phishing is mostly done with a fake caller ID.
-
Keyloggers
Keyloggers refer to the malware used to identify inputs from the keyboard. The information is sent to the hackers who will decipher passwords and other types of information. To prevent key loggers from accessing personal information, secure websites provide options to use mouse clicks to make entries through the virtual keyboard.
-
Smishing (SMS Phishing)
Phishing conducted via Short Message Service (SMS), a telephone-based text messaging service. A smishing text, for example, attempts to entice a victim into revealing personal information via a link that leads to a phishing website.
-
Trojan
A Trojan horse is a type of malware designed to mislead the user with an action that looks legitimate, but actually allows unauthorized access to the user account to collect credentials through the local machine. The acquired information is then transmitted to cybercriminals.
-
Malware
Phishing scams involving malware require it to be run on the user’s computer. The malware is usually attached to the email sent to the user by the phishers. Once you click on the link, the malware will start functioning. Sometimes, the malware may also be attached to downloadable files.
-
Malvertising
Malvertising is malicious advertising that contains active scripts designed to download malware or force unwanted content onto your computer. Exploits in Adobe PDF and Flash are the most common methods used in malvertisements.
-
Ransomware
Ransomware denies access to a device or files until a ransom has been paid. Ransomware for PC's is malware that gets installed on a user’s workstation using a social engineering attack where the user gets tricked in clicking on a link, opening an attachment, or clicking on malvertising.
-
Website Forgery
Forged websites are built by hackers made to look exactly like legitimate websites. The goal of website forgery is to get users to enter information that could be used to defraud or launch further attacks against the victim.
-
Domain Spoofing
One example is CEO fraud and similar attacks. The victim gets an email that looks like it's coming from the boss or a colleague, with the attacker asking for things like W-2 information or funds transfers.
-
Evil Twin Wi-Fi
Hackers use devices like a pineapple - a tool used by hackers containing two radios to set up their own wi-fi network. They will use a popular name like AT&T Wi-Fi, which is pretty common in a lot of public places. If you're not paying attention and access the network controlled by hackers, they can intercept any info you may enter in your session like banking data.
-
Social Engineering
Users can be manipulated into clicking questionable content for many different technical and social reasons. For example, a malicious attachment might at first glance look like an invoice related to your job. Hackers count on victims not thinking twice before infecting the network.
Phishing Examples
Classic Phishing Email
Over the past few years online service providers have been stepping up their security game by messaging customers when they detect unusual or worrisome activity on their users' accounts. Not surprisingly, the bad guys are using this to their advantage. Many are designed poorly with bad grammar, etc. but others look legitimate enough for someone to click if they weren't paying close attention:
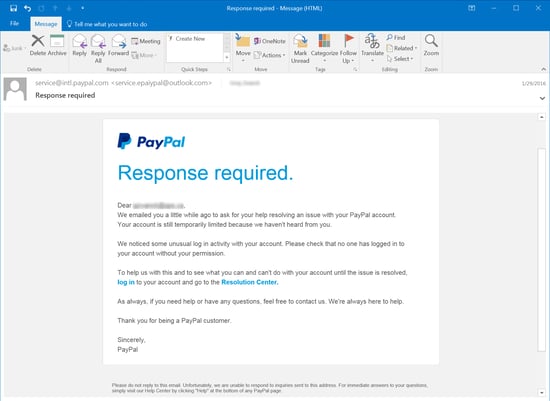
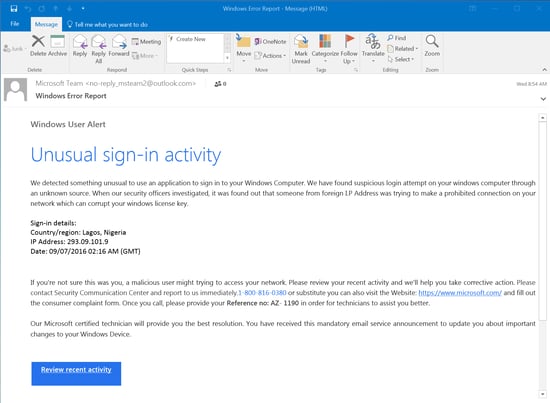
Consider this fake Paypal security notice warning potential marks of "unusual log in activity" on their accounts. Hovering over the links would be enough to stop you from ending up on a credentials stealing web site. The first example is a fake Microsoft notice, almost identical in appearance to an actual notice from Microsoft concerning "Unusual sign-in activity". The second example email points users to a phony 1-800 number instead of kicking users to a credentials phish.
Infected Attachments
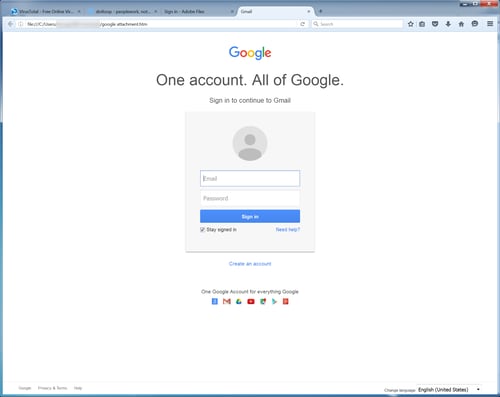
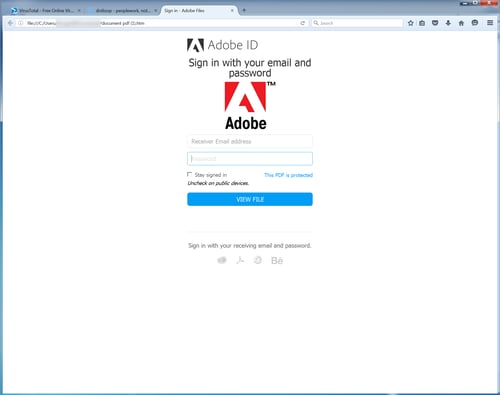
Malicious .HTML attachments aren't seen as often as .JS or .DOC file attachments, but they are desirable for a couple of reasons. First, there is a low chance of antivirus detection since .HTML files are not commonly associated with email-borne attacks. Second, .HTML attachments are commonly used by banks and other financial institutions so people are used to seeing them in their inboxes. Here are a few examples of credential phishes we've seen using this attack vector.
Malicious macros in phishing emails have become an increasingly common way of delivering ransomware in the past year. These documents too often get past antivirus programs with no problem. The phishing emails contain a sense of urgency for the recipient and as you can see in the below screenshot, the documents step users through the process. If users fail to enable the macros, the attack is unsuccessful.

Social Media Exploits
Several Facebook users received messages in their Messenger accounts from other users already familiar to them. The message consisted of a single .SVG (Scaleable Vector Graphic) image file which, notably, bypassed Facebook's file extensions filter. Users who clicked the file to open it were redirected to a spoofed Youtube page that prompted users to install two Chrome extensions allegedly needed to view the (non-existent) video on the page.


For most users, the two Chrome extensions were used to allow the malware a limited degree of self-propagation by exploiting the "browser's access to your Facebook account in order to secretly message all your Facebook friends with the same SVG image file."
On some users' PCs the embedded Javascript also downloaded and launched Nemucod [PDF], a trojan downloader with a long history of pulling down a wide variety of malicious payloads on compromised PCs. Users unlucky enough to encounter this version of the malicious script saw their PCs being taken hostage by Locky ransomware.
LinkedIn has been the focus of online scams and phishing attacks for a number of years now, primarily because of the wealth of data it offers on employees at corporations. Malicious actors mine that data to identify potential marks for business email compromise attacks, including wire transfer and W-2 social engineering scams, as well as a number of other creative ruses. Here are some examples we've seen through KnowBe4's Phish Alert Button:
In one case a user reported receiving a standard Wells Fargo credentials phish through LinkedIn's InMail:

Note that this particular InMail appears to have originated from a fake Wells Fargo account. The supplied link leads to a fairly typical credentials phish (hosted on a malicious domain since taken down):

It looks like the bad guys set up a fake Wells Fargo profile in an attempt to appear more authentic.
Another similar phish was delivered to an email account outside of LinkedIn:

This email was delivered through LinkedIn, as did the URLs used for the several links included in the footer of this email ("Reply," "Not interested," "View Wells's LinkedIn profile"):

Those URLs were obviously auto-generated by LinkedIn itself when the malicious actors used LinkedIn's messaging features to generate this phish, which hit the external email account of the mark (as opposed to his InMail box, as was the case in the first phish discussed above).
CEO Fraud Scams
Here's an example of a KnowBe4 customer being a target for CEO fraud. The employee initially responded, then remembered her training and instead reported the email using the Phish Alert Button, alerting her IT department to the fraud attempt.
When the employee failed to proceed with the wire transfer, she got another email from the bad guys, who probably thought it was payday:

Mobile Phishing
Mobile phishing attacks have increased by 85% every year since 2011, according to a recent report by Lookout. Attacks on mobile devices are nothing new, however they are gaining momentum as a corporate attack vector. Attackers now take advantage of SMS, as well as some of today’s most popular and highly used social media apps and messaging platforms, such as WhatsApp, Facebook Messenger, and Instagram, as a means of phishing. Security professionals who overlook these new routes of attack put their organizations at risk.
Here are just a few phishing related risks posed by mobile device use:
- Apps - lack built-in security. Free apps usually ask for a lot of access they shouldn’t need.
- WiFi - your device typically picks up the strongest signal, which may be a rogue WiFi that seems legitimate but is actually an attacker just waiting to monitor, intercept or even alter communications from your device.
- Bluetooth - can be used to spread viruses, and hackers can use it to hack into phones to access and exploit your organization’s data.
- Human error - thieves sell lost and stolen devices to buyers who are more interested in the data that the device itself.
- Smishing - aka phishing conducted via SMS. Similar to phishing emails, an example of a smishing text might attempts to entice a victim into revealing personal information. asking the recipient to take action on any number of seemingly mundane activities, i.e., the user’s bank claiming it has detected unusual activity or a congratulatory notice saying the person has won a prize from their favorite store.